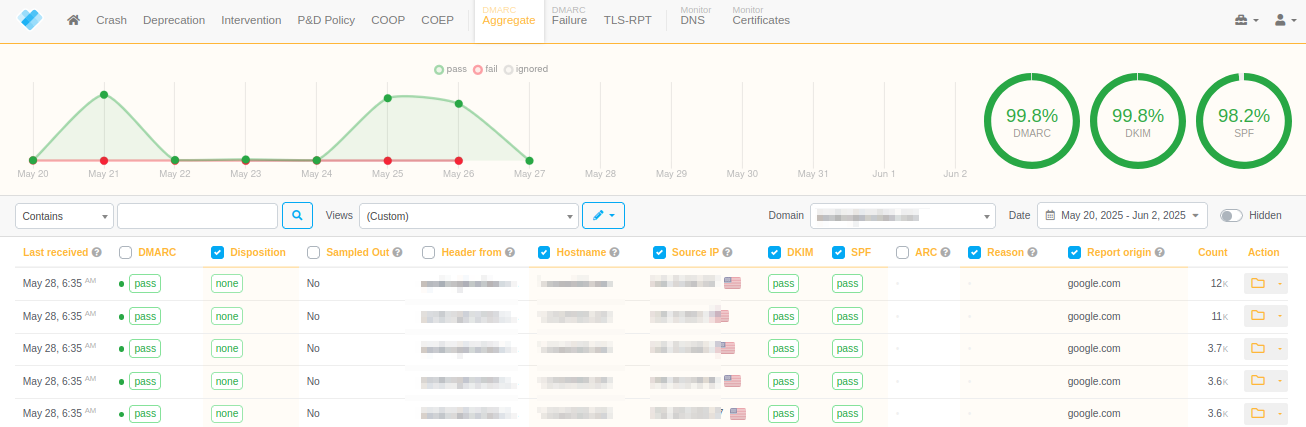
Why DMARC Monitoring
Monitoring your email flow with DMARC (Domain-based Message Authentication, Reporting, and Conformance) reports is essential for maintaining domain security, protecting your reputation, and ensuring email deliverability.
DMARC, combined with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), helps verify the authenticity of emails sent from your domain.
Below are real-world examples illustrating the critical role of DMARC monitoring in identifying and resolving email issues
- Transitioning to Cloudflare DNS: We recently assisted a client whose email compliance was disrupted following a migration of their domain’s DNS to Cloudflare, managed by well-intentioned web consultants. The issue arose because the Cloudflare Proxy feature was enabled, which inadvertently affected several critical DNS records (e.g., CNAME and A records). This misconfiguration broke compliance for the primary method the client used to communicate with their customers.
- Uncovering Unauthorized Email Activity A university discovered through DMARC reports that 30 million emails were being sent daily under their domain without their knowledge. This was possible because their DMARC policy was set to p=none, which permits domain spoofing. Many IT consultants leave DMARC policies at p=none, exposing organizations to such risks.
- Protecting Your Domain Reputation A small business we assisted was being spoofed, leading to a tarnished domain reputation. As a result, their legitimate emails were ignored by some email providers. DMARC reports identified this as an internal “provider policy” issue, even though the domain wasn’t listed on public blacklists.
- Detecting Configuration Changes in Contact Forms “Help! We’re no longer receiving emails from our contact form.” A new web developer had changed the configuration, causing emails to originate from an unauthorized IP address. Our email monitoring service detected this misconfiguration, enabling a swift resolution.
- Identifying Issues with Ticket Systems “Help! Our ticket system is no longer operational.” Monitoring revealed that tickets were being routed through a different provider and were not signed with DKIM, among other issues. This allowed us to identify and fix the problem quickly.
- Ensuring Platform Compatibility “We’re no longer receiving client feedback via eBay/Shopify/XYZ.” Monitoring showed that the platform was no longer directing traffic through authorized IP addresses, causing email delivery failures.
- Preventing Quarantine of Legitimate Emails “I sent 500 emails, and they all went to quarantine!” Monitoring revealed that the emails were sent from a new email platform not specified in the domain’s SPF record, leading to delivery issues.
- Avoiding DNS Misconfigurations “Our last email campaign was rejected by most recipients!” Our DNS monitoring service detected a second DNS TXT (SPF) entry added for a new campaign tool. Having multiple SPF records is not permitted, and this misconfiguration caused the campaign’s failure.
- Adapting to New Email Services “Why are so many of our emails suddenly being quarantined?” The domain was initially configured to use Google Workspace as an authorized email sender. However, the client began using Microsoft 365 without updating the configuration. Our email monitoring service identified this issue, allowing us to authorize Microsoft 365 and restore deliverability.
- Handling Sporadic IP Address Changes Previously compliant outgoing emails were suddenly rejected or quarantined due to sporadic changes in the IP address ranges used for sending (not specified in the SPF record). This issue arose after a change in the reseller hosting the email service on Microsoft 365. Additionally, some providers, during infrastructure changes or major issues, send emails through unlisted IP ranges not included in their include:theirdomain SPF records, which monitoring helped identify.
- Responding to Recipient Policy Changes A customer reported being unable to reach domains hosted by Microsoft or a major bank in their country. After updating their DMARC policy to a stricter setting (e.g., p=quarantine or p=reject), their emails were accepted. Monitoring revealed that Microsoft and the bank had tightened their email security policies, which would have gone unnoticed without DMARC reports.
- Exceeding SPF DNS Lookup Limits A new technician, unaware of the 10 DNS lookup limit for SPF, added an include:something entry, rendering the SPF record non-compliant. Monitoring detected this issue, preventing widespread email delivery failures.
- Addressing Issues with Third-Party Apps A client using a Shopify app to send reports to clients, resellers, and end users found that these reports were no longer sent from IP addresses specified in their SPF record and lacked DKIM signatures. As a result, the client’s DMARC policy caused these emails to be rejected. Monitoring pinpointed the issue for correction.
- Mitigating Spoofing During Temporary Policy Changes A client left their DMARC policy at p=none during temporary changes, resulting in thousands of spoofed emails sent daily under their domain (visible in the RFC5322.From/Header From field). These emails, promoting a religious group, originated from a university network in the United States. Monitoring alerted the client to this abuse.
- Handling Phishing Complaints Another client with a p=none DMARC policy suddenly received hundreds of daily complaints because their domain was used in phishing campaigns. DMARC monitoring helped identify and address the issue promptly.
- Uncovering Hidden Provider Policies A client’s SPF-, DKIM-, and DMARC-compliant emails were inexplicably deleted when sent to a specific domain or provider. DMARC reports revealed that the recipient had an internal policy to discard these emails, allowing the client to take corrective action.
- Avoiding Overly Strict SPF Configurations A client changed their SPF record to use a -all (strict) mechanism, which caused random DKIM authentication failures and led to the rejection of outgoing emails. Monitoring identified this misconfiguration, preventing further email loss.
Conclusion
DMARC reports and email monitoring services provide critical visibility into your email ecosystem, enabling you to detect unauthorized activity, adapt to configuration changes, and maintain domain reputation.
By proactively monitoring SPF, DKIM, and DMARC settings, you can "improve" reliable email delivery, protect your organization from spoofing and phishing, and avoid costly disruptions.
Updated October 10, 2025